For almost a decade—and counting—ransomware has been a massive security headache for individuals and businesses alike. More than just some malicious codes, it’s now considered a type of terrorism or a weapon of war.
The good news is that you can prevent ransomware without spending any money. You only need to understand how it works and avoid it.
This post will explain ransomware in layperson’s terms and how you can keep yourself safe from this scam. The key is to pay attention and take the issue seriously.
Dong’s note: I originally published this post on May 24, 2018, and updated it on November 5, 2022, with more practical information on how to stay safe.
What is ransomware, and why is it so bad?
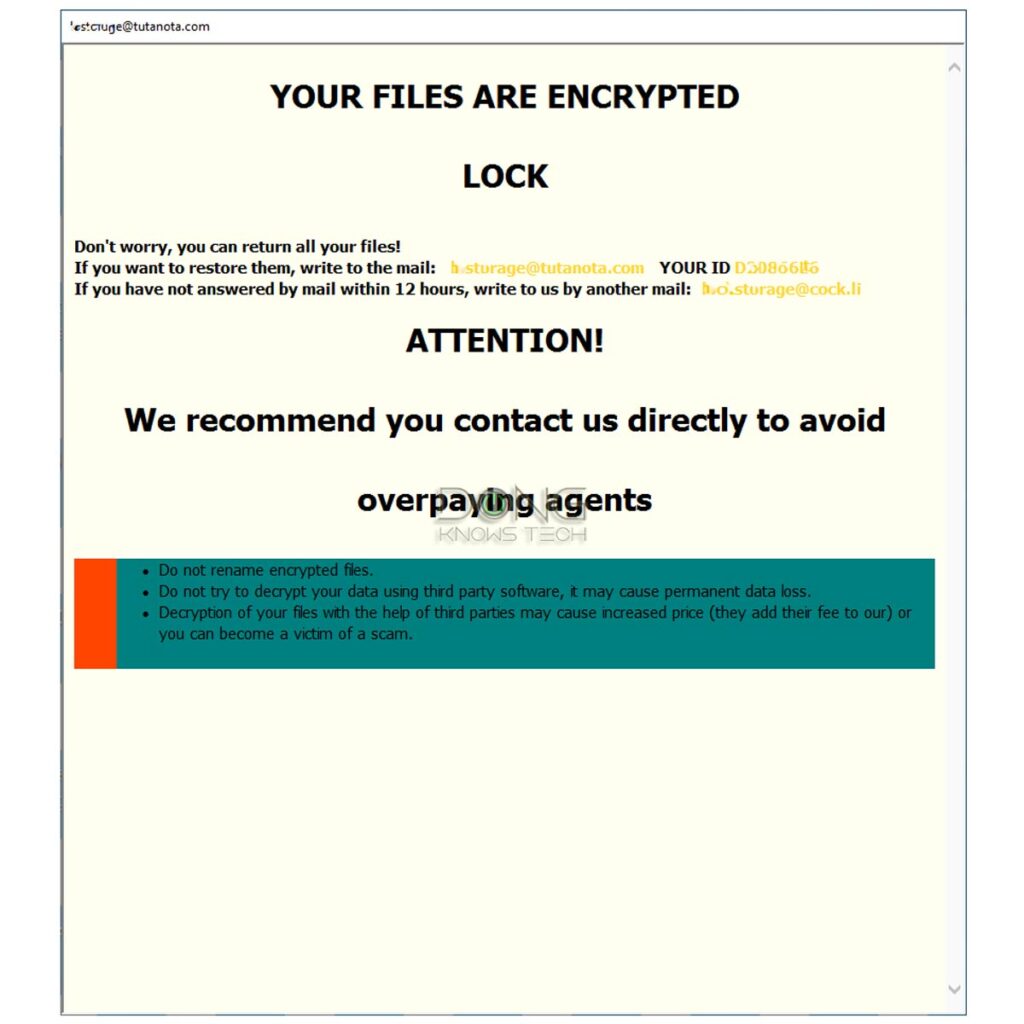
Ransomware is a piece of malicious software that, when executed, encrypts—or locks—popular file types, causing you to be unable to open documents or even run applications.
The malware then displays a message with instructions on how you can pay—usually via cryptocurrencies—to get your files back.
You can think of ransomware as an event where somebody comes into your home and sprays a generally impossible-to-remove glue all over your furniture and appliances, rendering them inaccessible or useless. That person then demands payment to clean up that glue with a secret method only they know.
When you see that dreadful message, you better hope you’ve had an alternative way to restore your data—via particular backups. Otherwise, chances are you will never get your files back. It’s just too late.
That’s because the ransom tends to be prohibitively high, and when you start paying, you’ll have to keep paying because the bad guys can release a portion of data at a time.
On top of that, chances are you won’t get your data back 100 percent intact. Among other things, they might lose their holding folder, date, time, or other attributes.
It’s tough to clean any glue off thoroughly.
And sometimes, the ransomware is of “low quality” that even its owner can’t undo the damage. That happens.
By the way, paying the ransom means you support the practice, which worsens the matter. So, it’s never a good idea to pay in the first place. The point is, ransomware can be as big a headache as one that ends your business or career.
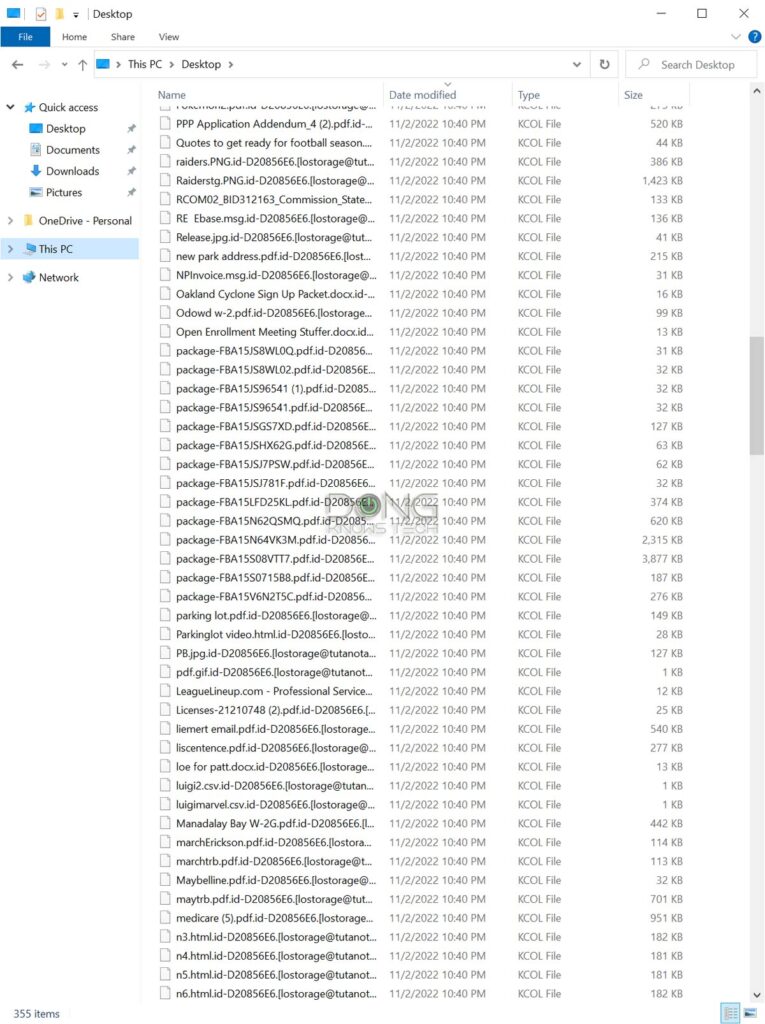
How you get infected
One thing is generally true: Ransomware does not install itself. It’s not a virus. Just like any software, it requires user interaction to execute.
That’s similar to using any software on the computer, such as the web browser, Zoom, or Skype—you first need to download and install it.
So, a user must interact with the computer and allow ransomware to download and launch the attack.
You have to open the door for that stranger with the glue-spraying can to come in.
That said, there are two ways ransomware can get into a computer:
- Most likely: The user is tricked into believing they are doing something benign (again, like downloading the Zoom app). Or
- Less likely: The bad guys manage to access your computer remotely and then install and run the malware themselves.
For this reason, a ransomware attack is always somewhat of an “inside job”—somebody must have full access to your computer to make it happen. And that means two things:
- It’s tough to prevent. It can take as little as one or a few misclicks to get infected, and the damage takes a short time to happen on a large scale.
- The damage is extensive. All files on the computers and all accessible network resources are susceptible. Therefore, in an office, expect all shared folders to be vulnerable.
In a ransomware attack, you generally don’t “lose” any data—nothing was taken away—you only lose access to it. Locking data up is much faster than taking it, contributing to how bad ransomware is.
There are many variants of ransomware. It’s relatively easy to change a few lines of code to create a new variant. These days, ransomware is available to certain parties as a service. One can order it, facilitate the damage, and split the ransom payment with the maker.
When a new variant is out, even the best protection software can’t stop it from executing. Antivirus and anti-malware applications are generally one step behind.
Nowadays, most ransomware variants remove themselves after having done the damage, making it hard to trace them back to their origin or even to find out what type it is.
The point is there’s a large window where everyone can be vulnerable. You should always try to prevent ransomware from infecting your computer and have contingency plans for the case it does.
How to prevent ransomware
The best way to avoid ransomware is to take precautions and always practice safety measures. The good news is that you can stay 100% safe from it if you remain alert.
If you don’t let that stranger in your home, he can’t spray glue on your furniture.
Good ransomware prevention practices
That said, there are two main ways to keep your computer safe.
1. Respect your computer’s warnings!
Downloading ransomware on your computer alone might not be the end game yet. It is when you execute (a.k.a “run,” “open,” or “view”) it that causes trouble.
In many cases, downloading and running a piece of software are combined in a single action. So, clicking on an embedded link within an email message alone might mean you’re about to execute some malicious code.
Here’s the good news: When you’re about to do something that can alter the system, the computer always confirms that with you via a User Account Control message. It’s your last chance to stay safe.
When a pop-up asks whether you want to proceed, take your time to make sure before responding affirmatively. Don’t just click on “Yes,” “OK,” “Run,” etc., without knowing what will happen as a result.
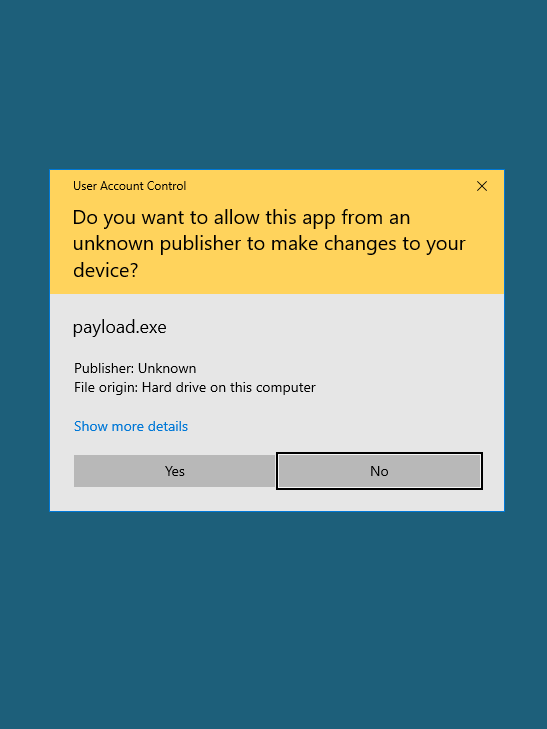
Staying vigilant is, by far, the most effective way to keep your computer safe from anything, including ransomware.
Extra: You got hit. What now?
What to do when you accidentally download and run a ransomware
If you’ve just accidentally downloaded (and run) ransomware—and are somehow aware of that—here’s what you should do:
- Turn your computer off immediately by unplugging it from power (or pressing and holding the power button for a few seconds). Ransomware needs time to encrypt the entire computer and network folders, and it can’t do that if the computer is turned off.
- Take all internal and external storage devices out of your computer and connect them to another to copy your data.
- Perform a re-partitioning (format) or discard the old storage devices.
Call a professional if you’re unfamiliar with steps #2 and #3. But you must do #1 immediately. Leaving your computer on will only make things worse. Don’t be curious!
Some folks I know turned their computer back on to “get just that one file I need” and ended up losing everything.
Keep in mind that some ransomware variants don’t attack immediately but wait until the computer is idle to do the evil deeds. The point is the chance you recognize that your computer is under attack can be rare.
But if you think you’ve been infected or are seeing evidence of that—the machine might act odd or has a lot of unusual activities—turn the computer off immediately and call a professional. That’s your only chance to stop an attack or limit the damages.
2. Keep your computer safe from unintended access
This part is a lot more complicated. The objective is to ensure nobody can use or manipulate your computer without your permission or knowledge.
You might need to do more than keep your password secure. The following are what you should generally do.
- Stay alert: Assume that you’re vulnerable and maintain vigilance. Again, it only takes a few seconds (via a few mindless mouse clicks) to get infected.
- Stay updated: Keep your computer updated with the latest security updates.
- Strong passwords: Always use strong passwords and keep them safe. (By the way, complexity is not associated with security regarding passwords. Instead, use a private hard-to-guess one that’s easy for you to remember and use. It can be a sentence, a long string of numbers, or a mix of both.)
- Beware of attachments/embedded links: Do not automatically open email attachments or click on embedded links from an email, chat screen, or social media without knowing it’s safe. (Generally, by hovering the mouse on the hypertext, you can preview the entire link on the status bar at the bottom of the window.)
- Use protection software and keep it up to date. The software might give you more warnings before you’re about to execute some suspicious codes. However, don’t rely solely on protection software; the last line of defense is always you, the user. (Windows 10 users: Use the built-in Windows Security app—more below.)
- Turn your computer off: Leaving your computer on 24/7 wastes energy and gives bad guys more time to mess with your system from afar. So, turn it off when you’re ready to call it a day.
- Set up remote access correctly: Do not turn on remote access unless you intend to use it. When you turn it on, ensure you know how to do that safely. The most basic is to change the default port number. Also, using strong passwords is a must.
How to minimize and manage ransomware’s damages
Trying to prevent ransomware alone is always good, but not enough. It would be best to assume that all of the measures above might fail—we’re all susceptible to mistakes. So, it’s a good idea to prepare if you get infected.
Here’s a sad truth: If your computer gets ransomware, there will be damage. What we’re doing here is trying to manage or minimize that. Chances are, you will need to rebuild your computer from scratch. The key here is to keep your data safe.
And the only way to make sure your data is safe is via a good backup practice. Again, regular and proper backups are the only way to keep your information intact against a ransomware attack.
Good and proper here means the backup should not be readily available to the user. If the backups are accessible by the infected account’s owner during the attack, they are also encrypted and become useless.
General guidelines on good and proper backup
Back up regularly—this is a daily (if not hourly) matter.
- For homes:
- Take a backup offline. An example of offline backup is alternating backups on two or more external drives and disconnecting each drive after a backup job or each day. You always have a set of backups that are not connected to a computer.
- Use some cloud backup service. In my experience, some, like Google Drive and Microsoft OneDrive, are smart enough not to back up data that’s encrypted by ransomware, and most give enough free online storage for your important data.
- For an office, use the home backups above and also consider the following:
- Use a different user account for the backup job and prevent other users from accessing the backups.
- Use a NAS server—I’d recommend one from Synology—as the backup destination. These servers can keep versions of their data using Snapshots (shadow copies), allowing you to restore if their share folders are infected.
If you use a Windows computer/server as a backup destination, turn on the Shadow Copy feature on that computer.
If a Windows server itself is infected, Shadow Copy doesn’t help since ransomware tends to delete all local shadow copies as part of its infection. So, again, make sure the server’s admin account, the one you use for making the backups, is safe by keeping its password secure.
And that’s it. If you follow the backup guidelines above, your data will be safe, even if you’re infected with ransomware. You might still need to hire somebody to restore the data, but the cost will be substantially less than paying the ransom.
Extra: Ransomware and Windows
The latest Windows operating systems have a feature that helps keep your data safe in the event of a ransomware attack.
How to prevent ransomware attacks using Windows Security
Windows 10 and 11 have built-in Windows Security Center with a Ransomware protection feature that keeps your files safe when the computer is infected.
Here’s how it works: This feature preemptively limits the full access (read and write) to specific folders and only allows pre-approved applications to change the content inside these folders. Other apps only have read-only access.
Microsoft determines these “whitelisted” applications automatically and generally includes common apps. However, you can also manually add other apps to the allowlist. Ransomware, by default, is not on the list and, therefore, won’t be able to make changes to your files to do any harm.
In other words, Windows 10’s ransomware protection feature adds another protective layer around your data by allowing only “known” or approved apps to change your data. As a result, your information is safe even if your computer has ransomware.
Using this method does have a significant downside: Many legit apps will not work correctly until you manually put them on the allowed list. But that’s a small price to pay considering the otherwise.
If you’re using a third-party antivirus program, Windows Security is generally disabled. If the third-party protection software has no ransomware-related features, it’s best to remove it and use Windows Security, which is free.
Steps to turn on ransomware protection on Windows 10 or Windows 11
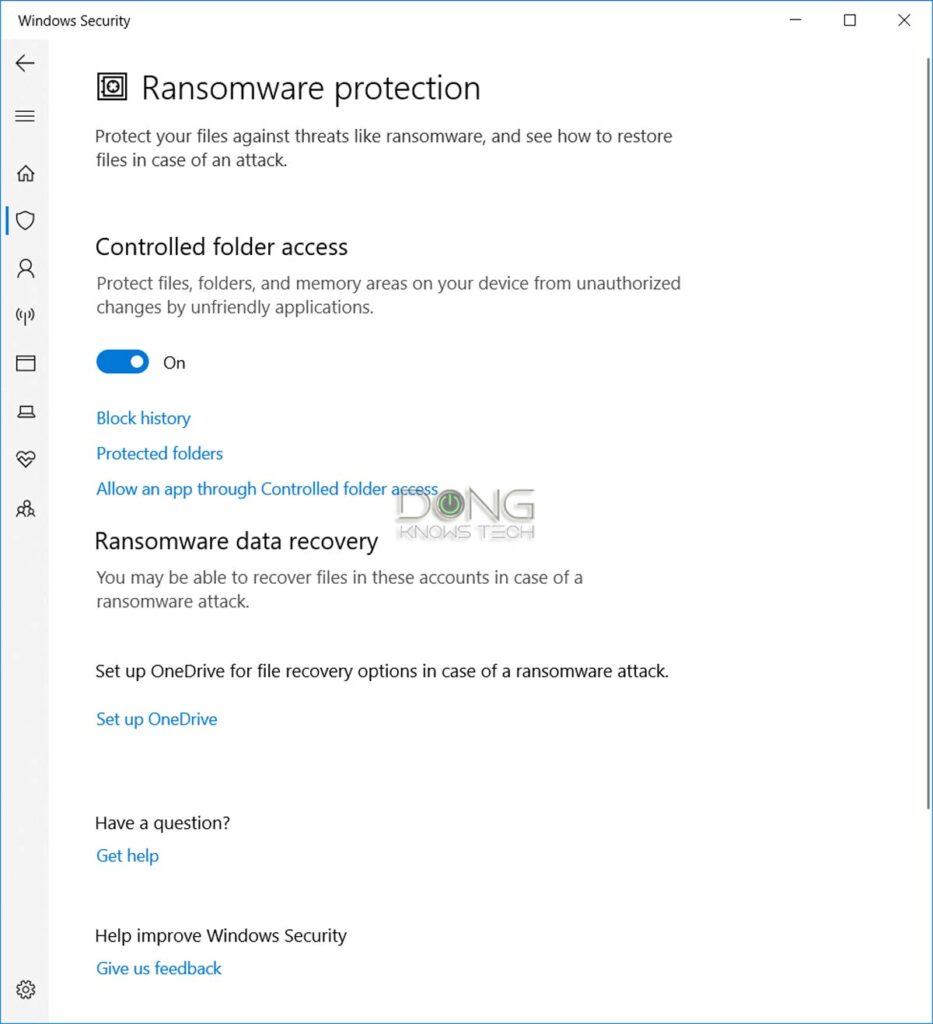
- Click on the search field by the right of the Start button (lower-left corner) and search for Ransomware Protection. As it appears on the Start Menu, click on it—the Ransomware Protection page of Windows Security will appear.
- Under Controlled folder access, slide the switch to the On position. Click on Yes to the User Account Control prompt.
- Click on Protected Folders. All the folders in the current profile (Documents, Pictures, Music, etc.) are already there. You can add or remove other folders of your choice, including network-shared folders, by clicking on the plus (+) sign.
- Click on Allow an app through Controlled folder access. Here, you can add more apps of your choosing to have full access to the content of protected folders by clicking on Add an allowed app. If you’re not sure, leave this list blank.
By the way, on this page, you can also set up OneDrive to get additional backup and protection. OneDrive gives you 5GB of free online storage, enough for essential documents.
And that’s it! From now on, your data is safe even when your computer is under a ransomware attack. (Still, don’t count on this 100%, make sure you also do the backups mentioned above.)
Again, remember that this feature might block good software from accessing your data. You might note some software, like a scanner or photo editor, might show errors. In this case, you’ll need to repeat step #4 and add the applications to the list of allowed apps.
Final thoughts
In the first few days of November 2022, I ran into multiple ransomware-related situations—the risks are currently extremely high.
All of those were resolved without data loss, thanks to proper backups. Still, they collectively cost the owners thousands of dollars in labor and new hardware. That’s not to mention the loss of productivity and the headaches.
Ransomware is a type of evil that occurs like a heart attack: out of the blue and often without warning.
So, let me repeat this: Ransomware is a type of evil that occurs like a heart attack: out of the blue and often without warning. Just because everything works fine doesn’t mean it won’t happen to you.
So, check on your precious data right now and, at the very least, make a backup before it’s too late. Stay safe!




One of the best way to mitigate ransomware is to air-gap your backups, like those usb drives you mentioned.
But NAS units are so much more convenient, and because they can be programmed to be turn on and off automatically, you can easily have 2x nas units that each turn on, on alternate days to be the destination for backups. Then the process becomes automatic and you won’t accidentally forget or some other ‘life’ event that endangers your data. 🙂
tools ransomware malware auto fix
There’s no such tools, D.
I believe in prevention is better then cure. Using network based firewall system is best approach and it is more then easy now a days to get such solutions.
I agree on better safe than sorry, Manny. But no firewall can 100% prevent ransomware if you download it and run it as mentioned in the post.
Good advice. I image my system drive all the time.
Way to go, Morse!
Thanks Dong
Sure, Victor! 🙂