This post will explain NAS security—you’ll know when to worry and when not to—and offer tips on securing your server’s data against hacking attempts and accidental or malicious deletion/alteration.
This applies to those with a NAS server. So, get yourself one if you haven’t. I’d recommend a Synology. I used the brand as an example for this post.
At the gist, this is a matter of keeping the (admin) user account safe and having the option to return files or folders to a previous state.
While backing up data regularly is important, that’s not enough against ransomware since such attacks can corrupt data on a connected backup device, too.
When you’re through, you’ll have that sense of certainty in data security no matter what situation you get yourself in.

How to keep your data safe: Use a NAS server
For data security, here’s my general practice with a (Synology) NAS server:
- Store important data on the server by:
- keeping files and folders on the server, applicable within a local network, via shared folders.
- syncing/backing up data from the computer and the server. This can be done via the local network or the Internet.
- Keeping the data on the server safe by:
- protect the admin user account of the server.
- have backups and, most importantly, shadow copies as a contingency plan in case of attacks.
You can read all about #1 in my other posts on Synology and NAS servers. Or you can start with this piece on network storage basics.
This post tackles #2. It’s about NAS security.
Note on data security
There’s no absolute security. That’s the case in the cyber world and real life as well. (As long as we’re alive, we’re at risk of dying to an extent.) Security only means minimizing the risks.
Keeping data safe generally means making it hard for unauthorized parties to access or manipulate it. The data is secure when it’s harder for the parties to access it than how much it’s worth to them.
Security is about a deterrent.
Understanding NAS server security: Threats vs. hacks
A server is generally online at all times. It’s best to assume that it’s under constant threats. That’s the case with any device hooked to the Internet—some remote parties are always trying to hack into it.
But that doesn’t necessarily mean your server is inherently in danger.
In the cyber world, hacking (or breaking in) is when an unauthorized party (or parties) manages to take control of a device, often remotely over the Internet, fully or partially, to download the information it stores, destroy it, or whatnot.
In the case of ransomware attacks, the purpose is clear: the bad guys want to hold your data hostage to extract money.
While many out there want to hack into your device, it doesn’t mean they can. The majority of the time, these attempts fail.
You can think of your server as your house—there’s no hiding it from the earth’s surface, and you can’t stop folks from looking at it, coming to its front, or even walking around it to check for unlocked doors and so on.
In fact, we assume all of the above, which is why we have locks on doors in the first place. And if your doors are locked securely, and there are no holes in the walls, your house is safe no matter how much other folks might want to get inside. The same reason why banks exist.
On an average day, each among over a dozen NAS servers I manage gets its ports scanned—a practice similar to having your home’s door handle pulled to see if it’s unlocked—thousands of times. None has ever been breached. And that’s been the case for more than a decade.
Not to butcher the analogy: Folks can literally break into your property in real life with a hammer or even a rock.
On the Internet, there’s no way for any party to smash the actual server hardware remotely—it’s a different type of “break-in.”
I don’t mean to downplay the severity of online threats. But it’s also not helpful to exaggerate them.
The point is that just because there are many threats doesn’t mean they are all credible. And it’s best to focus on keeping your server secure instead of listening to the hype about the potential dangers.
Let’s go into the details.
Synology NAS Security: Steps to keep your server safe
A party can access a server in two ways: via a security vulnerability (called an exploit) or an existing legit user account.
Back to the house analogy, the former is like a hole in your wall, whereas the latter is like accessing the door via a duplicate key or a leaked lock combo.
We have to deal with each differently.
How to secure a server that has a known vulnerability
There’s not much you can do when a server has a known vulnerability other than to install the latest security update that fixes it.
With a Synology server and most servers, you can set the update to happen automatically on a schedule.
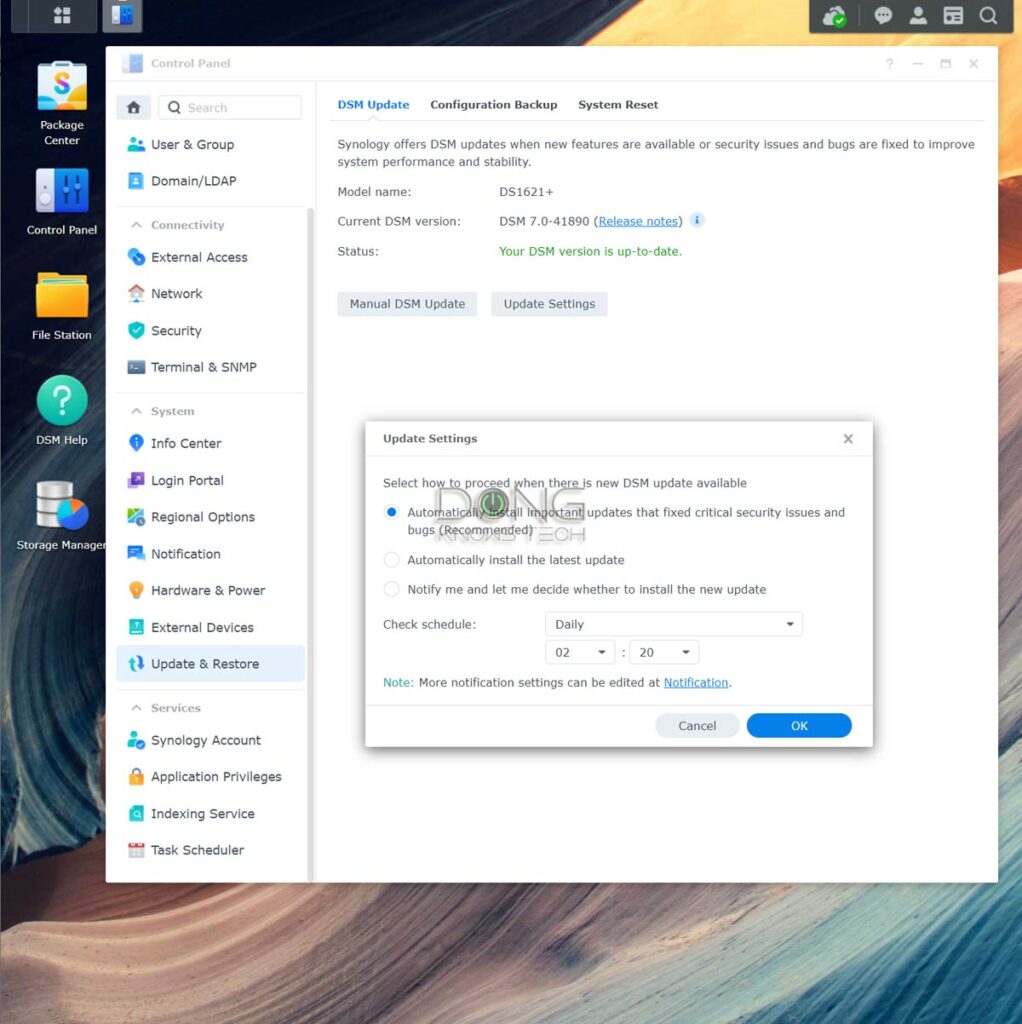
If there’s a known vulnerability and there’s no security patch, you need to do the following:
- Turn your server off or take it offline—don’t connect it to the Internet—until the security patch is available. Depending on the issues, there might be other tweaks, just like the case of any operating system. Or
- Get a new server.
Securing a server by keeping user accounts safe
With no known vulnerabilities, you can keep your server safe simply via proper user account management.
Generally, in this case, hackers can only gain access to a server via brute force attacks—they keep guessing the usernames and passwords until they get a combination that works. And they use software to try hundreds, if not thousands, of combinations per second.
Keeping your login info secure is like protecting the key to your home—putting it under the doormat on the outside is generally not a good idea.
The good news is it’s relatively easy to fight against this type of break-in attempt. You only need a good user account policy and an effective mechanism to auto-block the “guessing.”
And that brings us to user account management.
Rules on user accounts
Here are what you should do with the user accounts:
- Disabled the default admin account. This is because it’s a known account—hackers already know the username, which is “admin” or “administrator”; they only need to figure out the password. Disabling this account literally makes it at least twice as hard to guess the login info.
- Do not use an account with administrator privileges for general data access. Use it only for server management and data recovery. In other words, don’t give admin privileges to just any account.
- Use multiple (random) words for a username. For example, instead of “Dong”, use “Dong Ngo” or “DongN”. Basically, avoid known, popular names like “David” or “John”.
- Use a hard-to-guess password. You don’t need to use an overly complex one and risk forgetting it. For example, “MyName1sD0ng” (note the “1” and “0”) is a tough password to guess, yet, quite easy to remember.
- Use 2-factor authentication (2FA), which is available in Synology DSM 7, at least with the server’s admin accounts.
The 2FA implemented by Synology is quite well-thought-out. You can handle that via a single tap on the phone and save a device to a safe list so that 2FA is not needed in the subsequent logins for a period.
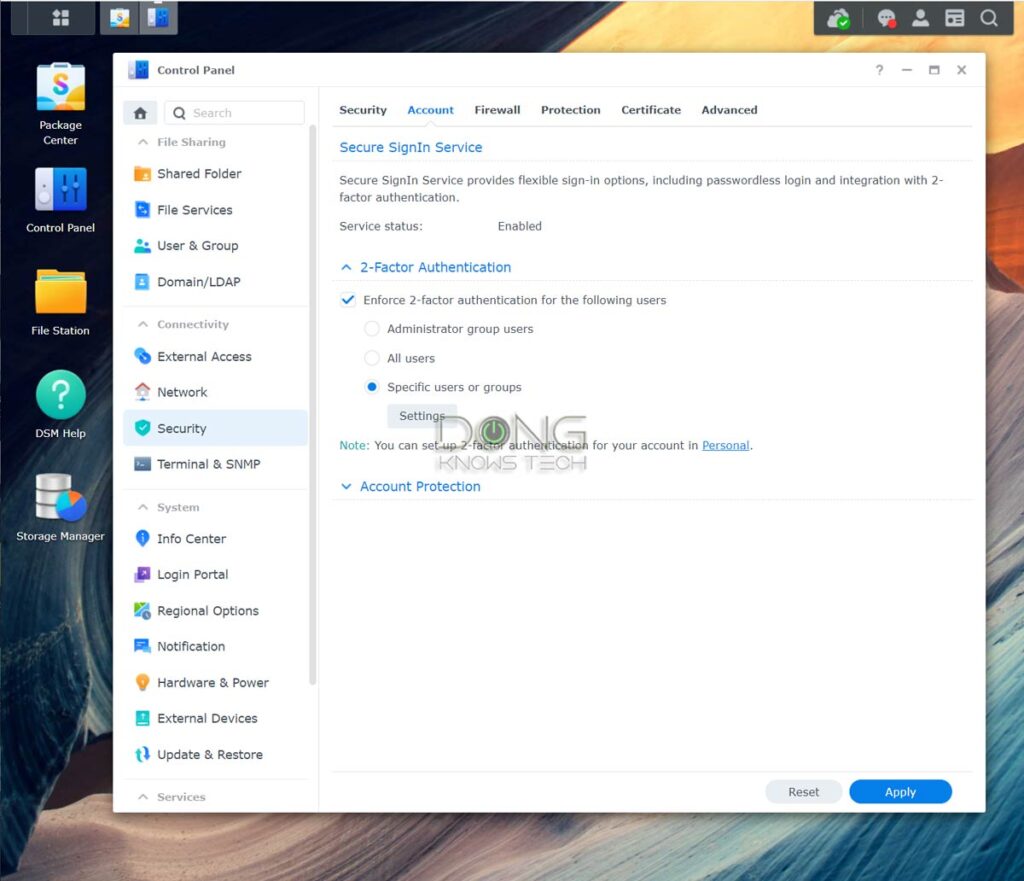
With a strong password and 2FA enabled, you can be sure the account is safe. But there’s more you can do.
Steps to keep user accounts safe
Auto-blocking is an excellent way to fight against brute-force attacks.
After certain incorrect entries for the username or password, you can block an IP address permanently or for some time, keeping the server safe from the particular source of attacks.
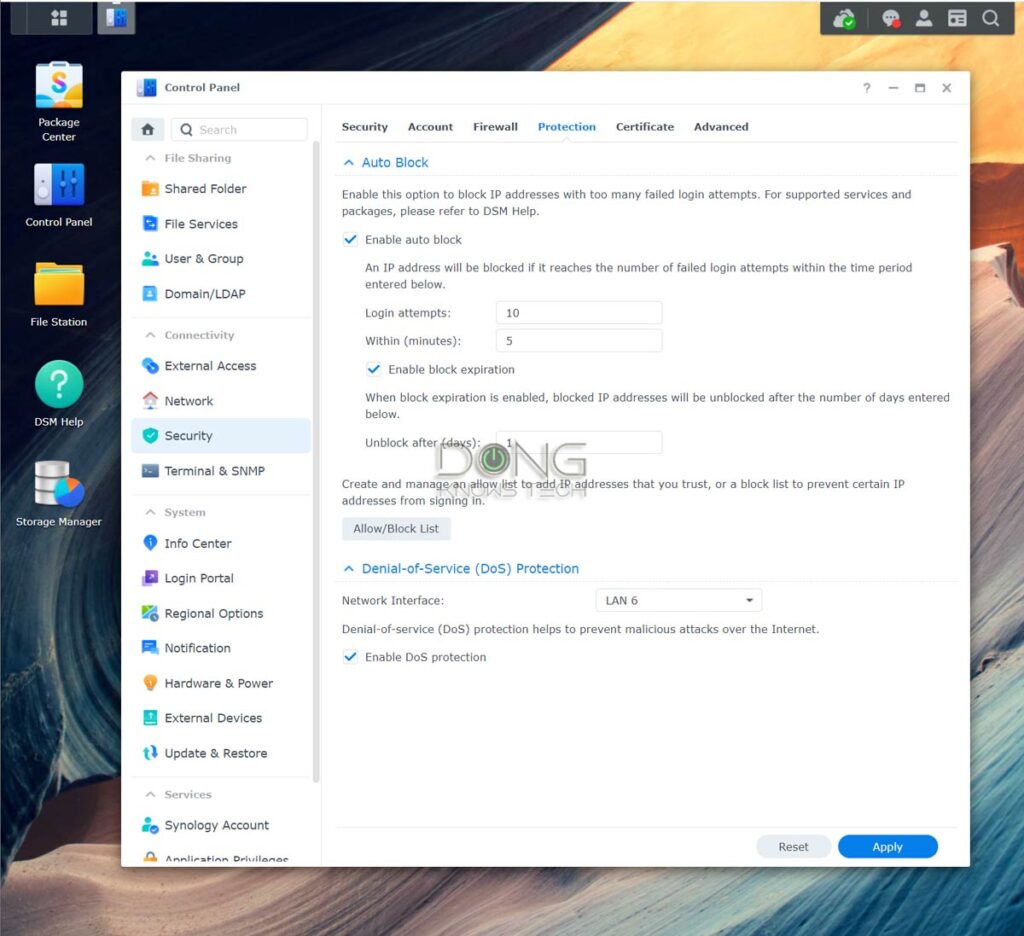
How to enable Auto IP blocking on a Synology NAS server
- Log in to the server’s interface, open Control Panel
- Go to Security and then Protection tab
- Under Auto Block, check the box that reads Enable auto block
- Specify the parameters. Generally, fewer login attempts within a more extended period mean better protection. For example, the settings of 10 attempts within 5 minutes are more than enough to block any brute-force attack. But 5 attempts within 20 minutes will make it many times safer.
- Check the Enable Block expiration and give it a value if need be. If you don’t, the IP will be blocked permanently until you manually unblock it. Generally, you should allow the expiration if you have remote users—sometimes, folks forget their logins.
How to enable Auto Account Protection on a Synology NAS server
Account Protection will automatically temporarily lock out an account if the username is used with a wrong password a specified number of times.
By the way, this is why you shouldn’t use an easy-to-guess username, as mentioned above—your account might get locked out regularly.
- Log in to the server’s interface, open Control Panel
- Go to Security and then the Account tab
- Under Account Protection, check the box that reads Enable Account Protection.
- Specify the parameters similar to the case of the IP blocking above.
- Specify a time to Cancel Account Protection. If not, you might risk blocking a legit account permanently.
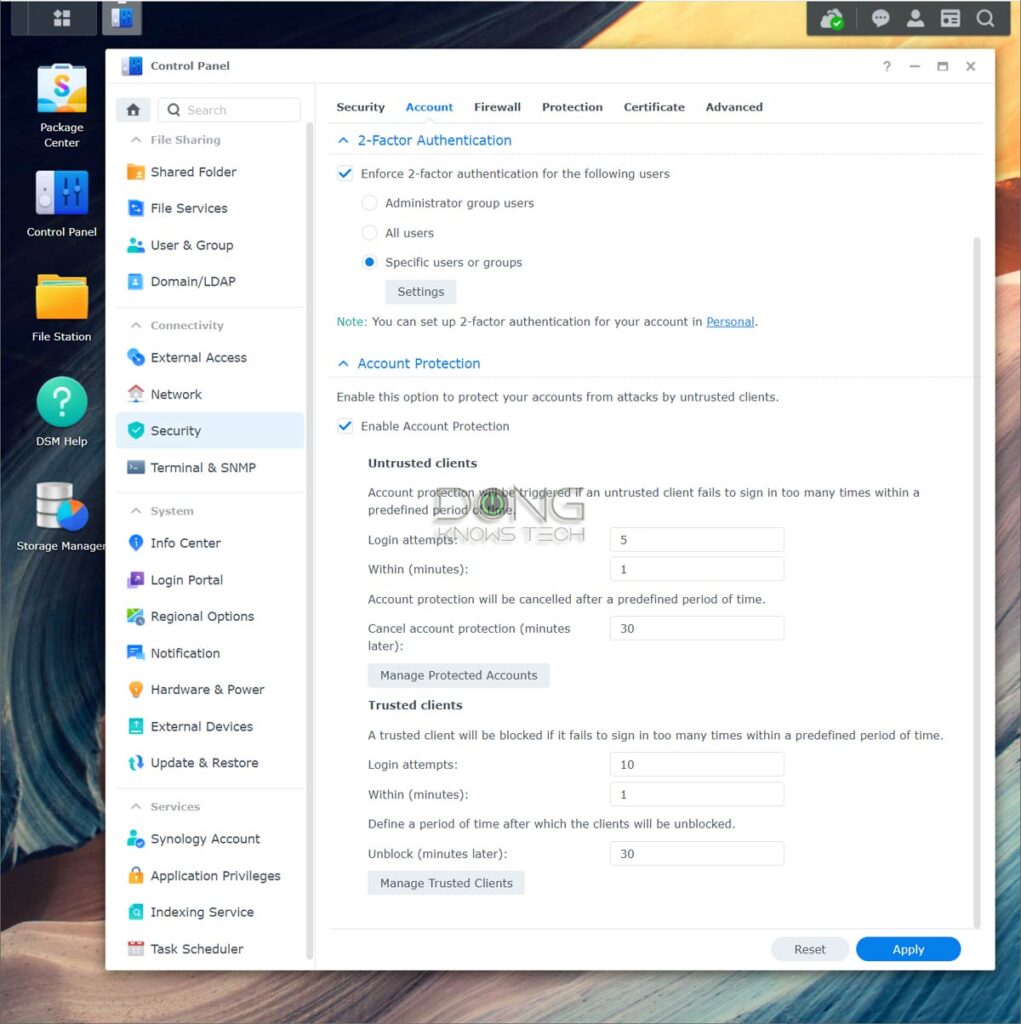
There are different Account Protection policies for untrusted or trusted clients. It’s OK to assume all clients to be the former.
Additionally, Synology has more security settings you can try, though unnecessary. You also run the Security Advisor app and follow its suggestions on High and Severe issues.
And that’s it. Your server is now safe.
It’s good to keep a balance between security and usability. If you board your house up, it is more secure, but you can hardly live in it.
Again, security is a matter of degrees.
NAS security and your data: How to keep your information intact
Keeping your server safe from unauthorized access is great but not enough for data integrity.
Sometimes, bad things come from parties with legit access to the server. For example, if a network computer has ransomware, shared folders on your server are susceptible, too.
Generally, it’s best to assume that somebody will mess up and have appropriate contingency plans.
Managing data on a server
You can do a lot of things with a NAS server. But no matter what type of applications you use, there are generally two scenarios in terms of data storage:
- You’re accessing data stored directly on the server. This applies to shared folders, streaming content, databases, websites, etc. This is when the live version of your data is on the server. Or
- You store a copy of your data on the server. This applies when you use the server to sync data between devices or as the backup destination. This is when you have the live or production version of data elsewhere.
Either case has pros and cons—and sometimes you must use one or the other—but both are susceptible to malicious or accidental data alteration.
For example, you might inadvertently edit a document, remove an import paragraph, save the changes, and close it. Now, having the option to bring that document back to the previous state before the edit is crucial.
And this brings us to a valuable feature of Synology NAS servers, the Snapshot.
Enable Synology Snapshot
Available in all Synology servers that support the Btrfs file system, which is the case of most servers, Snapshot is part of an add-on package called Snapshot Replication.
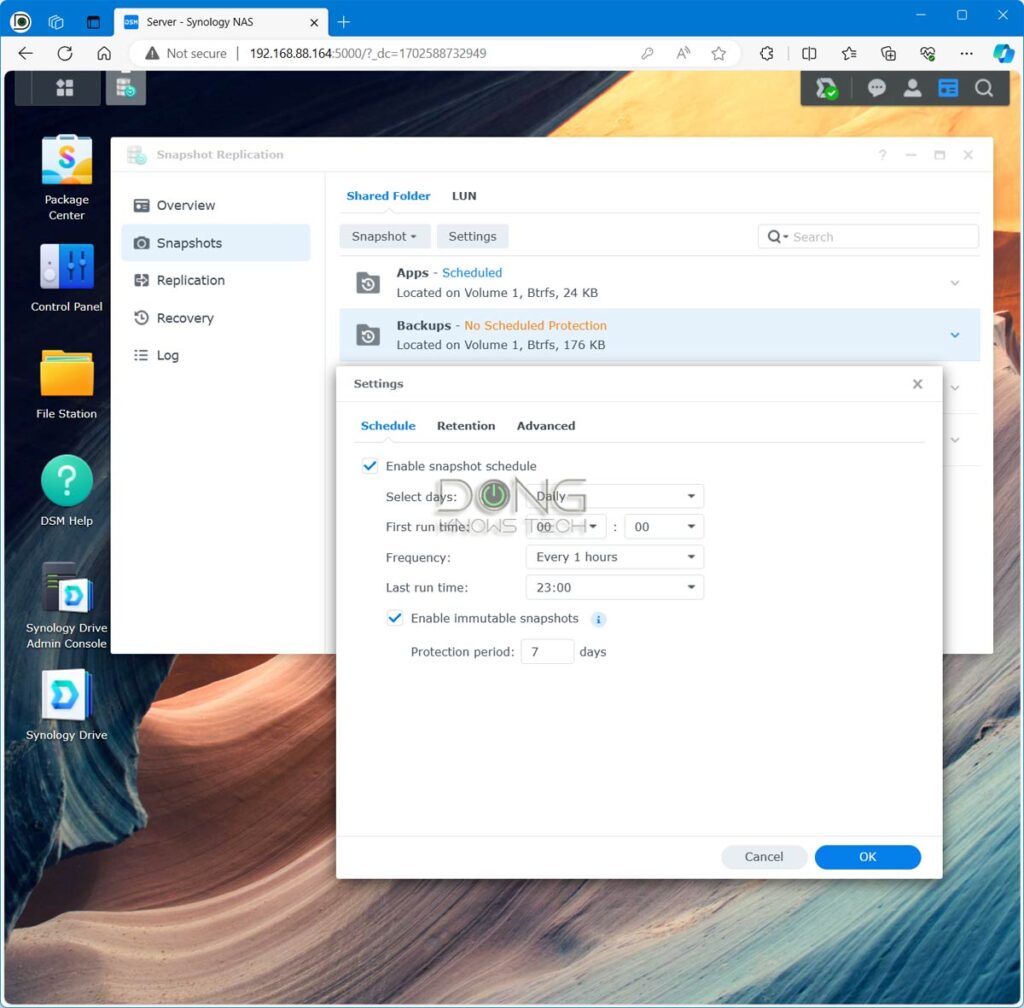
The Snapshot portion works similarly to Shadow Copy of Windows. When turned on, Snapshot automatically creates a version (snapshot) of the shared folder as frequently as every five minutes. You can retain up to 1024 snapshots of the data to quickly restore in case of mishaps or ransomware attacks—each snapshot can be view as a separate read-only shared folder.
The takeaway
There you go. Your server is likely safer than those security alarms make you feel.
No, you shouldn’t take data security lightly, but your data is secure as long as you keep the (admin) user account safe and have contingency plans against attacks and accidents.
Two major bullet points to keep in mind:
- Have good password policies, keep your server up-to-date, and have a tight Snapshot (file versioning) schedule for each important shared folder.
- Consider real-time server-to-server backups, folder sync, or replication if you have serious data. Don’t forget to also use file versioning for the backup server.
Once you’ve had those in place, you have little or nothing to worry about. I speak from experience.
Dong’s note: I first published this post on July 26, 2019, on server security and upgraded it on April 28, 2023, to add relevant information.



No one mentioned it yet but your title is a bit awkwardly phrased…
NAS Security: How to a Synology to Secure Data against Attacks and Accidents.
Keep up the good reviews.
Cheers
Fixed. Thanks, Moe. Typos is my middle name. 😳
Dear Dong, do you believe it is necessary to activate protections against Spectre and Meltdown vulnerabilities?
Unless you use an old OS, these vulnerabilities hardly affects home or SMB users, if at all, today. And there’s no protection you can activate against them. Upgrade your system to an appropriate OS version is the only way. Chances are you’re already using a safe OS.
so if I use a strong password + 2FA + limit failed login attempts, is it safe to access my server using a remote open WiFi connection that has no password required. like a free WiFi when traveling.
“Safe” is relative, Edgar. But I’d have no issue doing that — make sure you use HTTPS on the server. I’ve been doing that for years. If you want to be safer, use a VPN.
Hello Dong.
Thank you for all the advice on the website.
My Synology DS116does not support Snapshot replication.
What is the alternative please.
Thank you
You need one that supports the Btrfs file system, Cheeky. So either get a new NAS or use a backup drive via the USB and use backup versions. It’s not as effective but it works.
Is it useful to install any antivirus or malware apps on the NAS? I see two: Antivirus by McAffee, Antivirus Essentials.
It doesn’t hurt. But that’s mostly to protect clients since you generally don’t run random software on the server.
Is it even safer to enable the two factor authentication on the NAS?
Yes, of course, Francois. But it’s important to balance between safety and usability, too. 🙂