In a home network, everything goes through the router. As a result, when your home Wi-Fi router’s security is not up to snuff, many things can go wrong in your local network, and you might not be aware of that. However, security is also a matter of degree.
This post will explain steps to keep your Wi-Fi router secure enough for you to have peace of mind. If you want your network to be absolutely secure, turn Wi-Fi off and disconnect the router from the Internet.

Home Wi-Fi router security: How to keep your network safe
To have a local network, you need a router, and preferably no more than one. Nowadays, a home router tends to have a built-in Wi-Fi access point. It’s a Wi-Fi router. In many cases, that router is extended by more broadcasters. That’s when you use a Wi-Fi system. However, it’s always the router unit that handles security.
While it’s relatively easy to keep wired devices out of your network—you can simply unplug their network cables. Things are more complicated with Wi-Fi devices and remote parties on the Internet. The former are designed to connect wirelessly, and the latter may try to get in through your broadband connection. Both happen behind the scenes with no visible signs. Keep that in mind.
Routers are not created equal. Shapes and sizes aside, they are all differentiated by their firmware, which determines the router’s settings and features.
So, the first thing to keep in mind is that it’s best to get a router from a reputable networking vendor with long-term support—pick one from these best lists. After that, on the security front, there are two main types of routers to consider when it comes to home routers:
- Vendor-dependent routers: Those that must always connect to the vendor to work, such as Amazon’s eero, Google’s Wi-Fi/Nest, TP-Link’s Deco. They are app-operated hardware with limited features and settings.
- Vendor-independent routers: Those that can run independently without being connected to the hardware vendor. Examples are generally standard routers with an integrated web-based user interface from Ubiquiti, Asus, TP-Link, or Netgear.
Generally, with vendor-dependent routers, there’s not much you can do in terms of security other than the Wi-Fi password. Other security matters are at the mercy of the hardware vendor. That said, if you really care about having control over your network’s security, I’d recommend a standard router with a web user interface, accessible via its default IP address.
Tip
When logging into the web-based user interface of a home router or most devices, you might encounter a privacy/security error notice in which the browser suggests the webpage is potentially unsafe, similar to the screenshot below.
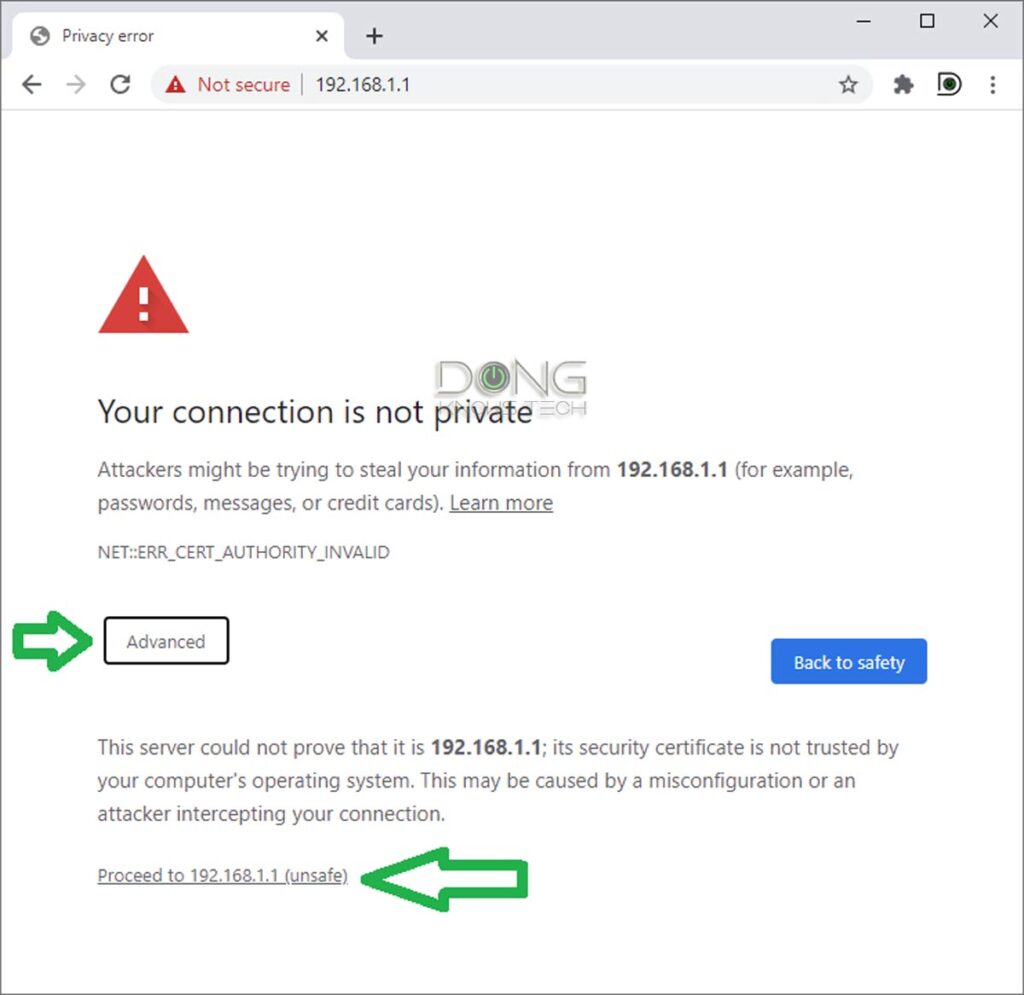
The reason is that the device’s built-in web server doesn’t have a mechanism to prove that it supports the now-required HTTPs protocol. For that, among other things, it needs to be signed by an external party.
It’s safe to ignore this notice and proceed to the interface when accessing a device within your local network.
Different browsers have slightly different warnings and ways to bypass them, but they all require clicking a few extra times. Pay close attention, and you’ll find out the way to proceed.
While many standard routers come with an option to link with a vendor account in return for added features or convenience, they don’t need to connect to the vendor before they can function.
With that, let’s move on to how to secure your home Wi-Fi router.
Common security items for home Wi-Fi router security
No matter which type of router you use, there are four things you can do with it to improve your network security, including:
- The admin password.
- The Wi-Fi password.
- The Guest network.
- The firmware.
If your network leverages special types of wiring other than standard network cables, that might require additional security. More on that in the posts on Powerline and MoCA.
With that, let’s go into the details of these four items.
1. The admin password: Make it unique and hard to guess
The admin password allows for changing the router settings. A person with this password has complete control over the network.
Some routers—especially ISP-provided gateways—have known default admin passwords. In this case, it’s best to change that password as soon as you start using a router. Even better, when possible, turn the username into something other than “admin” or “administrator.”
Nowadays, as a security practice, most routers’ initial setup process includes a step for you to change or create the admin password. In any case, make this password hard to guess and, most importantly, different from the Wi-Fi password. Again, this is the password used to manage the router, it’s not for any user to know.
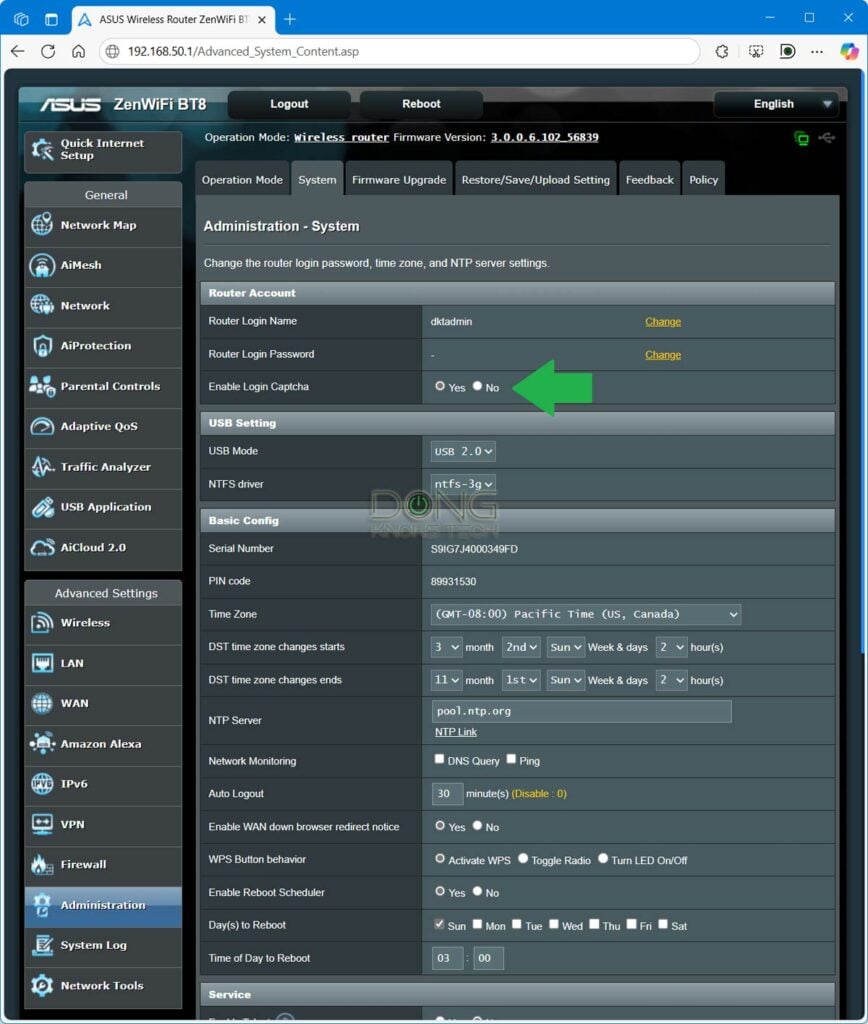
Some routers have a built-in CAPTCHA to ensure only a real person can log in. Others might even have two-factor authentication (2FA) for the admin access. If yours supports this added security feature for the admin access, turn it on.
1. The Wi-Fi password: Make it unique but easy to enter
A Wi-Fi network includes the network name (a.k.a SSID) and its password. The name itself is not a secret—it appears on any device. The part that is not seen and keeps the network secure is the password.
This password allows a device to connect to your Wi-Fi network. Knowing the Wi-Fi password, among other things, a person can:
- Use your internet connection.
- See your network resources, such as a file server, a printer, or a media streamer. However, it doesn’t necessarily mean they can access these resources. For example, if your server requires a separate login, they cannot view its content until they have that login.
- See your router’s IP address and, with the admin password, access its settings and control the network.
That said, again, you need to use a different password for your Wi-Fi from the one used for admin management above.
Tips
When it comes to passwords, it’s always about keeping them a secret that matters. Complexity is not always a positive attribute. The goal is to create a password that is both difficult to guess and easy to remember and use.
A Wi-Fi password that includes letters, numbers, uppercase and lowercase, and special characters can be a real pain, especially when you need to enter it into an IoT device, such as a printer or a media streamer—even a modern one like the Fire TV.
Generally, when it comes to Wi-Fi, it’s best to use a digit-only password. Here’s a way to make a password effective and easy to remember:
Pick a long sentence or phrase and use each word’s letter count to form the password.
If you use that previous sentence, the password would be 414833545652438—use another phrase for yourself. If you think you can’t remember the password, write that sentence down instead of the password itself.
If you want to offer somebody access to the Internet (1) and nothing else, a Guest Wi-Fi network comes into play.
3. The Guest Wi-Fi network
A Guest Wi-Fi network is a way to share your Internet connection without potentially compromising your entire system. It’s a fancy name for a virtual SSID network that’s isolated from your main one.
By default, the Guest network allows only access to the Internet but not to your local resources. Most routers include the Wi-Fi Guest network feature; you can turn it on via their web interface or mobile app.
A few things about setting up a Guest network:
- If you enable password protection, make the password different from the primary Wi-Fi network and the admin password.
- Keep the default setting that isolates the guest network. This setting generally tends to be “Access Intranet” (set to disabled) or “AP isolation” (enabled).
- If you give guest access to a lot of people, such as on a public network, it might be a good idea to limit the broadband bandwidth if that’s an option.
- You don’t need to name your Guest SSID with the word “guest” in it.
A Guest Wi-Fi network also comes in handy when you want to isolate specific devices from the rest of the main network, including those of your own.
4. The firmware: Keep it up to date and turn on protection features
Firmware is the operating system of a router. It decides how well a router works and how secure it is. Networking vendors often release new firmware versions to improve the router’s performance and security.
It’s a good idea to check for new firmware and update your router at least a few times a year, especially when there’s a security bulletin about your router or the networking vendor. While it’s generally best to use a router with its latest firmware, turning on the auto firmware update feature can cause issues such as unexpected interruption. That said, if you choose to use auto firmware update, pick a time that you know your network is idle.

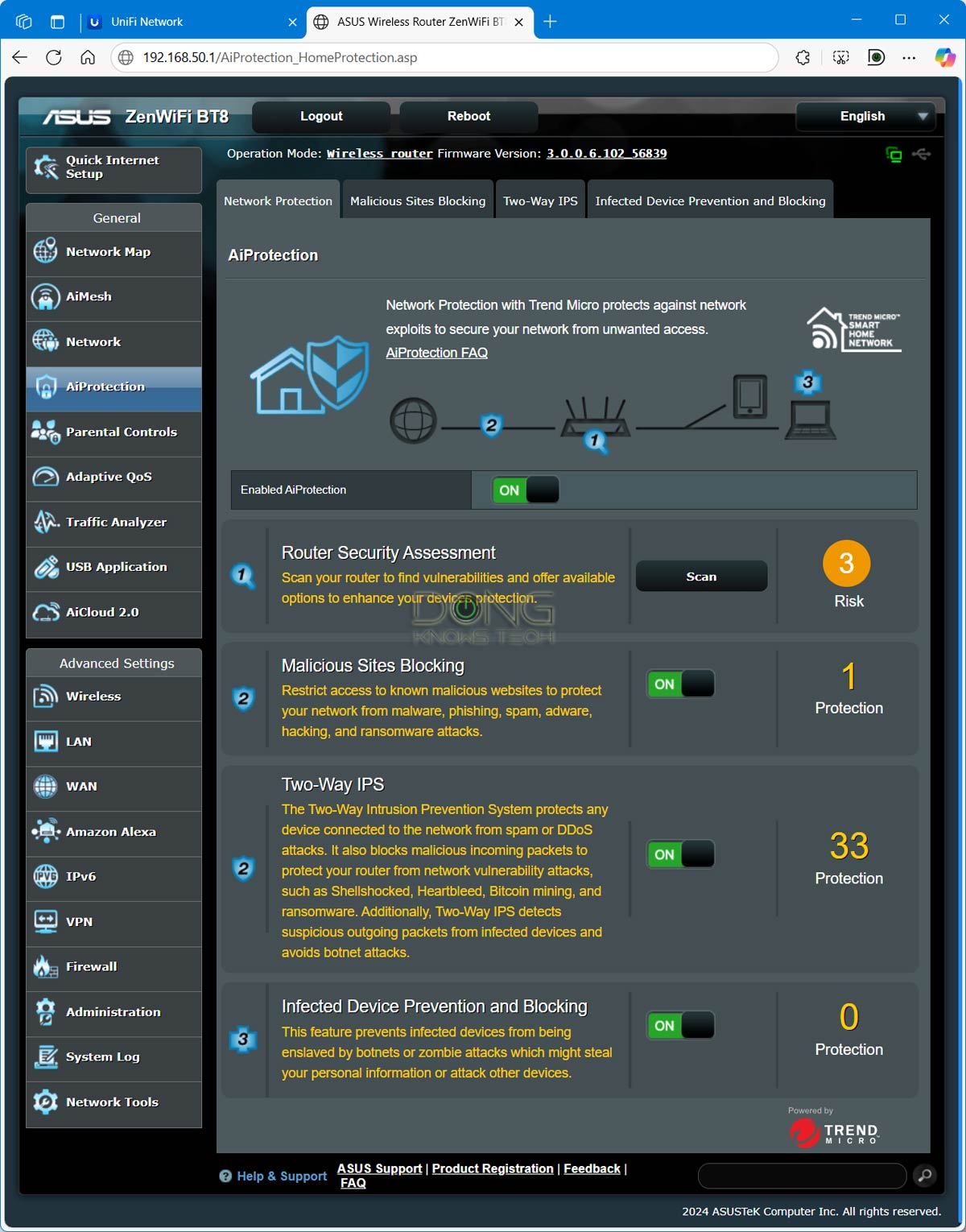
The second thing you can do with a router’s firmware is to turn on its included online protection feature. Not all router brands have this, but those from Ubiquiti’s UniFi lineup and Asus have excellent security features for free. Other brands, such as TP-Link and Netgear, also have this type of feature, but it might require an add-on premium.
The last thing about the firmware is to be aware of the remote access feature. Not all routers have this, and those that do always have it disabled by default. If you want to turn it on, it’s best to have a good understanding of the WAN IP address, Dynamic DNS, and port forwarding before enabling any remote access or management.
Signs that show your router has been hacked and how to rectify it
When targeting a router, hackers generally don’t intend to destroy it. Instead, they want to manipulate it to steal your information, such as usernames and passwords for a website or service you use.
That said, if your router has been compromised, chances are it still works like normal. But some things won’t work right. Here are the telltale signs that your router has been hacked:
- Your browser (Chrome, Firefox, Safari, etc.) often goes to unwanted websites, sometimes without you doing anything.
- You get unrelated, irrelevant, or spam results when doing an online search. Sometimes, it seems a different search engine than the one you pick (Google, Bing, etc.) is being used.
- When accessing your router’s web interface or mobile app, the admin password you created no longer works.
- The router’s DNS settings are different from “Auto” or what you have entered.
- There are settings you didn’t create, like a new Wi-Fi network or port-forwarding entries.

If your router has been hacked, the best and possibly the only way to fully repair it is a hard reset. After that, update its firmware to the latest and set up your network from scratch, in that order.
The takeaway
To summarize, to keep a tab on your home Wi-Fi router security, you first need a router that allows you to do so to a great degree. That usually means getting one that can work without first connecting to the vendor.
After that, change the admin password and, when possible, even the login username. Ensure the admin password differs from the Wi-Fi password and keep both secure.
And finally, when applicable, enable remote management only if you know how to use it safely. And keep your router patched with the latest firmware.
Security is nuanced. By default, every device connected to the Internet is vulnerable, much like as long as you live, you’re at risk of dying, to a degree. The only way to be absolutely secure is to turn that device off or when something ceases to exist.
As long as you follow these best practices mentioned here, you can consider your router, and hence your home network, safe to a reasonable degree applicable to most homes.
Dong’s note: I originally published this post on April 17, 2018, and last updated it on May 18, 2025, to add up-to-date, relevant information.



Dong.
Yet again, your posts are excellent. Thank You.
If only I had learned of you earlier ?? Installed (or rather tried to) to get the RT BE-88U up. Little did I know that Asus in its wisdom now uses 192.168.50.1 as the IP address. I installed my beloved AC88U in 2016, and nothing since, and in those days… it was always ….1.1
In sheer desperation I seemed to recall that you Did mention this change in one of your many excellent post. Dong, suffice it to say…at 81 this is becoming a young man’s game.
As always…. thank you so much for your reviews, reading them is often the highlight of my day. The BE-88U is a beautiful machine and I can only hope that in will proudly stand in the footsteps of the AC-88U. Paid about 180 dollars for it… brandnew, it seemed too good to miss.
BTW….. am too old to live in the fast lane Dong, so “Remote Access” is well and truly switched off. Tks for that advice.
Albert
Thanks for the posts. I am trying to figure out more about the “group key update period” found in the SSID/password settings. Do you recommend changing this to a certain number for increased security? (0? 3600? 86400?) Appreciate any thoughts or links!
Check out this post on Wi-Fi settings.
Hi Dong,
I liked your extra section on a way to create passwords. However, is there a reason we should not use a password manager with generator? Also, many sites require things like letters and special characters in a password rather than “just” a string of numbers. Thanks in advance for your comments.
The password I mentioned is only for your Wi-Fi network, Jerry, and generally the only restriction is 8 char length minimum.
In 2023 (almost 2024!), do you believe that “auto firmware update feature is generally not a good idea”, even for non-tech-savvy homes?
Moreover, if automatic firmware updates was a must-have feature, are there certain brands and/or models that you’d suggest?
I have to recommend a router to a few different family members (who both live in small homes) and I just don’t trust that they’ll periodically manually check for firmware updates.
That’s generally not a good idea no matter when. That’s like you have somebody come to your house and fix/change things around without you having any say about it — but sometime that’s necessary. So, that’s case-by-case depending on the hardware and vendors. But some new routers, like the Asus RT-BE96U, has auto update divided into two parts, security-only and the entire firmware. In that case, the former is OK.
Got it. Thanks! (And thanks for writing!)
👍
Hi Dong,
I noticed that DoS protection is not enabled on my Asus router (XD4) by default. Does this pose a security threat? Should I enable it?
Thanks
Not really, Jerry, and yes, that doesn’t hurt other than using a bit of the router’s processing power.
Generally, DoS attacks apply primarily to a business or a website that can’t shut down. You can restart a home router, which will stop the attacks since your WAN IP will likely change without affecting anything.
Hi Dong
I noticed that you did not mention WPS, UPNP, and Ping. Also no mention of DNS over TLS. While the last one is more of a privacy protocol, the former mentioned have always been an issue with router security. Has something changed to make them more secure?
Regards
Cranky
Most of what you mentioned have been hyped up in terms of security concerns, Cranky. In reality, I don’t think they have caused significant threats, if at all. They are just tools for “security experts” to brag about their “knowledge” or make money from views and clicks. Most new routers have those disabled by default anyway.
Just an FYI -Today’s email has a bad link to this article.
Thanks, Deirdre. I fixed it.
Hey Dong, I recently tried logging into my Netgear Admin page and couldn’t. The information was correct but, i still couldn’t login, so i followed your advice .
A couple of questions if you have the time.
1- If the router had been hacked, how do I check the settings to see if they weren’t changed? i.e., DNS; Port Forwarding.
2- I noticed that the initial Netgear page 192.168.1
was sending the password “Unencrypted “ why would Netgear allow this?
Once reset, the router is reverted back to default settings, David. That means all customized settings, including fraudulent ones, are gone. As for the message, that’s normal. More in this post.
Great article as always Dong. Quick question.
I don’t want to put you on the spot by recommending the best router, so, i will ask this, which one do you use?
In the article you mentioned, “Keep tabs on wifi router, if allowed to do so”- Which wifi routers allows its owners to do this?
Good question, David. After reading your comment, I decided to edit the post a bit to make things more clear. Give it another read.
Good morning Dong, I would like your thoughts on an issue I am having with my Netgear AC 4300 6 Stream router.
When I enter the router’s interface utilizing the 198.168 format, I am unable to get into the ADVANCED section of the routers interface to make adjustments to the security settings of the router.
The tab is there in the UPPER LEFT CORNER, but nothing occurs.
Your thoughts?
Use a different browser, David.
I’d love to see a post about best Routers for dealing with guest access and security. My 2500 square foot home with an attached AirBnB has a linksys with a guest option, which I thought was going to be great, but the guest option has zero security. Not cool; back on the market, but I have to say this is seldom something reviews mention much about…I have to dig to get a sense of how they handle guests, whether the guest account is only broadcast from the main router in a multi router system, what it’s security is, whether a different LAN is available for it, etc. Perhaps my case is too specific but it’s been a real headache to try to overlay reviews with getting that info.
Check out this post, Kayle. Part of it applies to your case. There’s no such router, by the way, since there’s no such thing as a “guest network”. It’s just a marketing term.
Great read. I’ll tell you a quick story that other first time readers may relate to. I decided to purchase my own Wi-Fi router and return the ISP’s rented one. I bought a Netgear R6300v2. The wife asked If I was setting it up right. I gave her that look, like really! How hard can it be? Within minutes I had downloaded the app and my network name and password was set. See, easy.
A few nights later I turned the router off to annoy the kids (fun to do, even to this day). A few moments later I found them back on their devices stealing the neighbors internet that had an open guest network. A little cheeky, but I was quietly amused by their ingenuity. The next time I saw them I told them what the girls were doing. He laughed and locked it down later that day. I told the wife “I have a password on our guest setup”. That was five years ago.
You know what’s been bothering me, Dong? So, over the years we’ve been adding devices (I think we’re up to 25 now) and every time we always see the same guy at the top of the list of available networks. Sometimes I’d get a little perturbed, I want to be number one, It’s my house. We always thought their Wi-Fi Kung fu was strong. Whoever they were had good taste in routers though. Theirs was a Netgear too. It told everyone who looked what it was. Okay, nice piece of kit I thought, but the owners aren’t very imaginative though. All the others have been given nice names. (I know Dong, you already know where this going).
Years went by. And with the kids now doing distance learning I started thinking of up grading our network. So I began researching all the new stuff – AX, Mesh, all with fancy new acronyms. Wait.. These things are still dual band. I thought I remember seeing dual band on this one when I got it. Anyway, started reading your reviews and finally here. Doh.
So my 5GHz band has never been used. Protected by a default passphrase that comes in every box. And I don’t want to talk about my router login through the web browser, I feel stupid enough. The good news is I found you.
So yesterday I followed your instructions. And sheepishly told the wife. The best way I could explain it was. We didn’t leave the front door wide open. But the key was under the mat.
I really don’t remember seeing a smart setup when I first installed it. And even if I did I would have bypassed it wanting to do it myself.
Dong, as you go about your day today and if you get the chance to read this. I’d like you to know in some small way you have made a difference in someones life. And I’d like to say, thank you.
Thanks for sharing, Scott. Glad you figured it out. 🙂
Hey Dong Ngo, I watched you a lot when you were on CNET. You and Brian Tong were my favorites. I just stumbled upon your site while I was researching networking equipment. I no longer watch CNET and am happy I found you again. Keep up the good work. Thank you for you passion!
Thanks for your support, Ike. BTW, BT has also gone indie and had his own YouTube channel. Check it out https://youtu.be/7J9CbU-BjqA !